Re: Cryptography repo on github not loading on Pharo 10
Hi Marcus,Yes I can do it, but the Cryptogrphy package relies on InputEventSensor to generate random seeds in this code:
RandomGenerator class>> unpredictableStringsDo: aBlock "Enumerate sources of information from my environment that should be generally hard to guess." | time | time := Time millisecondsToRun: [ aBlock value: World imageForm bits compressToByteArray ; value: Sensor mousePoint x asString ; value: Sensor mousePoint y asString ; value: Time millisecondClockValue asByteArray ; value: Date today asString ; value: Time now asString ; value: Display extent asString. 100 timesRepeat: [ aBlock value: UUID new ]. #(imagePath lastUpdateString systemInformationString shortImageName datedVersion lastQuitLogPosition licenseStringTemplate) collect: [ : each | aBlock value: (SmalltalkImage current perform: each) asByteArray ] ]. aBlock value: time asByteArray; "maybe the pointer has moved, hit it again." value: Sensor mousePoint asString ; value: Time millisecondClockValue asByteArray
I need to use PBKDF2, is there any alternative (running on Pharo 10) to this Cryptography package?
TIA
CheersDavide
On Thursday, November 30, 2023 at 12:48:49 PM GMT+1, Marcus Denker <marcus.denker@gmail.com> wrote:
You could add a class InputEventSensor (just a subclass of Object) to make the code load
(the package might want to add methods to that class?)
After that it will be easier to see why it relies on low level code like that.
Marcus
On 29 Nov 2023, at 16:14, Davide Varvello via Pharo-users pharo-users@lists.pharo.org wrote:
Nobody?
InputEventSensor is missing in Pharo 10.
There are also several unheard requests about InputEventSensor on Discord, see attachment.
Cheers
Davide
On Tuesday, November 28, 2023 at 02:43:18 PM GMT+1, Davide Varvello via Pharo-users pharo-users@lists.pharo.org wrote:
Hi Guys,
The crypto repo:
Metacello new
baseline: 'Cryptography';
repository: 'github://pharo-contributions/Cryptography';
load:'core'.
is not loading due to a dependency on InputEventSensor, can you help me please?
TIA
Davide
<SCR-20231129-oguq.png>
You can load the code and I think PBKDF2 does not rely on the troubling code. But when you do this you will see that it is way too slow. The number of iterations for modern crypto environment makes a single password action many seconds to complete.
I use the https://github.com/PierceNg/OpenSSL-Pharo library where I’ve added two methods
pbkdf2: password passwordLength: passlen salt: salt saltLength: saltlen iterations: iterations keySize: keySize result: result hashFunction: algo
^ self ffiCall: #(void PKCS5_PBKDF2_HMAC (const char* password, int passlen, const char* salt, int saltlen, int32 iterations, EVP_MD algo, uint32 keySize, uint8 result))
and
pbkdf2Password: password salt: salt iterations: iterations keySize: keySize
| result |
result := ByteArray new: keySize.
self
pbkdf2: password
passwordLength: password size
salt: salt
saltLength: salt size
iterations: iterations
keySize: keySize
result: result
hashFunction: LcEvpSHA256 new.
^ result
maybe this helps even if it is not a load and use option. The two methods can just be added as extension methods in your own code.
Norbert
Am 30.11.2023 um 16:32 schrieb Davide Varvello via Pharo-users pharo-users@lists.pharo.org:
Hi Marcus,
Yes I can do it, but the Cryptogrphy package relies on InputEventSensor to generate random seeds in this code:
RandomGenerator class>> unpredictableStringsDo: aBlock
"Enumerate sources of information from my environment that should be generally hard to guess."
| time |
time := Time millisecondsToRun:
[ aBlock
value: World imageForm bits compressToByteArray ;
value: Sensor mousePoint x asString ;
value: Sensor mousePoint y asString ;
value: Time millisecondClockValue asByteArray ;
value: Date today asString ;
value: Time now asString ;
value: Display extent asString.
100 timesRepeat: [ aBlock value: UUID new ].
#(imagePath lastUpdateString systemInformationString shortImageName datedVersion lastQuitLogPosition licenseStringTemplate) collect:
[ : each |
aBlock value: (SmalltalkImage current perform: each) asByteArray ] ].
aBlock
value: time asByteArray;
"maybe the pointer has moved, hit it again."
value: Sensor mousePoint asString ;
value: Time millisecondClockValue asByteArray
I need to use PBKDF2, is there any alternative (running on Pharo 10) to this Cryptography package?
TIA
Cheers
Davide
On Thursday, November 30, 2023 at 12:48:49 PM GMT+1, Marcus Denker marcus.denker@gmail.com wrote:
You could add a class InputEventSensor (just a subclass of Object) to make the code load
(the package might want to add methods to that class?)
After that it will be easier to see why it relies on low level code like that.
Marcus
On 29 Nov 2023, at 16:14, Davide Varvello via Pharo-users <pharo-users@lists.pharo.org mailto:pharo-users@lists.pharo.org> wrote:
Nobody?
InputEventSensor is missing in Pharo 10.
There are also several unheard requests about InputEventSensor on Discord, see attachment.
Cheers
Davide
On Tuesday, November 28, 2023 at 02:43:18 PM GMT+1, Davide Varvello via Pharo-users <pharo-users@lists.pharo.org mailto:pharo-users@lists.pharo.org> wrote:
Hi Guys,
The crypto repo:
Metacello new
baseline: 'Cryptography';
repository: 'github://pharo-contributions/Cryptography';
load:'core'.
is not loading due to a dependency on InputEventSensor, can you help me please?
TIA
Davide
<SCR-20231129-oguq.png>
Thank you, NorbertI'll use your approach, thank you very much
CheersDavide
On Thursday, November 30, 2023 at 11:06:09 PM GMT+1, Norbert Hartl <norbert@hartl.name> wrote:
You can load the code and I think PBKDF2 does not rely on the troubling code. But when you do this you will see that it is way too slow. The number of iterations for modern crypto environment makes a single password action many seconds to complete.
I use the https://github.com/PierceNg/OpenSSL-Pharo library where I’ve added two methods
pbkdf2: password passwordLength: passlen salt: salt saltLength: saltlen iterations: iterations keySize: keySize result: result hashFunction: algo ^ self ffiCall: #(void PKCS5_PBKDF2_HMAC (const char* password, int passlen, const char* salt, int saltlen, int32 iterations, EVP_MD algo, uint32 keySize, uint8 result))
and
pbkdf2Password: password salt: salt iterations: iterations keySize: keySize | result | result := ByteArray new: keySize. self pbkdf2: password passwordLength: password size salt: salt saltLength: salt size iterations: iterations keySize: keySize result: result hashFunction: LcEvpSHA256 new. ^ result
maybe this helps even if it is not a load and use option. The two methods can just be added as extension methods in your own code.
Norbert
Am 30.11.2023 um 16:32 schrieb Davide Varvello via Pharo-users pharo-users@lists.pharo.org:
Hi Marcus,Yes I can do it, but the Cryptogrphy package relies on InputEventSensor to generate random seeds in this code:
RandomGenerator class>> unpredictableStringsDo: aBlock "Enumerate sources of information from my environment that should be generally hard to guess." | time | time := Time millisecondsToRun: [ aBlock value: World imageForm bits compressToByteArray ; value: Sensor mousePoint x asString ; value: Sensor mousePoint y asString ; value: Time millisecondClockValue asByteArray ; value: Date today asString ; value: Time now asString ; value: Display extent asString. 100 timesRepeat: [ aBlock value: UUID new ]. #(imagePath lastUpdateString systemInformationString shortImageName datedVersion lastQuitLogPosition licenseStringTemplate) collect: [ : each | aBlock value: (SmalltalkImage current perform: each) asByteArray ] ]. aBlock value: time asByteArray; "maybe the pointer has moved, hit it again." value: Sensor mousePoint asString ; value: Time millisecondClockValue asByteArray
I need to use PBKDF2, is there any alternative (running on Pharo 10) to this Cryptography package?
TIA
CheersDavide
On Thursday, November 30, 2023 at 12:48:49 PM GMT+1, Marcus Denker <marcus.denker@gmail.com> wrote:
You could add a class InputEventSensor (just a subclass of Object) to make the code load
(the package might want to add methods to that class?)
After that it will be easier to see why it relies on low level code like that.
Marcus
On 29 Nov 2023, at 16:14, Davide Varvello via Pharo-users pharo-users@lists.pharo.org wrote:
Nobody?
InputEventSensor is missing in Pharo 10.
There are also several unheard requests about InputEventSensor on Discord, see attachment.
Cheers
Davide
On Tuesday, November 28, 2023 at 02:43:18 PM GMT+1, Davide Varvello via Pharo-users pharo-users@lists.pharo.org wrote:
Hi Guys,
The crypto repo:
Metacello new
baseline: 'Cryptography';
repository: 'github://pharo-contributions/Cryptography';
load:'core'.
is not loading due to a dependency on InputEventSensor, can you help me please?
TIA
Davide
<SCR-20231129-oguq.png>
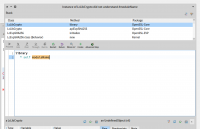
Hi NorbertI can't make your code working
I loaded the OpenSSL-Pharo lib, but when I run your code it gives me a DNU Exception: Instance of LcLibCrypto did not understand #moduleName.See screenshot
CheersDavide
On Thursday, November 30, 2023 at 11:06:09 PM GMT+1, Norbert Hartl <norbert@hartl.name> wrote:
You can load the code and I think PBKDF2 does not rely on the troubling code. But when you do this you will see that it is way too slow. The number of iterations for modern crypto environment makes a single password action many seconds to complete.
I use the https://github.com/PierceNg/OpenSSL-Pharo library where I’ve added two methods
pbkdf2: password passwordLength: passlen salt: salt saltLength: saltlen iterations: iterations keySize: keySize result: result hashFunction: algo ^ self ffiCall: #(void PKCS5_PBKDF2_HMAC (const char* password, int passlen, const char* salt, int saltlen, int32 iterations, EVP_MD algo, uint32 keySize, uint8 result))
and
pbkdf2Password: password salt: salt iterations: iterations keySize: keySize | result | result := ByteArray new: keySize. self pbkdf2: password passwordLength: password size salt: salt saltLength: salt size iterations: iterations keySize: keySize result: result hashFunction: LcEvpSHA256 new. ^ result
maybe this helps even if it is not a load and use option. The two methods can just be added as extension methods in your own code.
Norbert